We are living in a time when data privacy is a top concern for individuals. Given recent events, it’s easy to see why.

As many nonprofits already know, Blackbaud fell victim to a ransomware attack in May 2020. This was a hard hit during an already tough year for nonprofits.
If you’re grappling with how to handle the fallout of this data hack, both internally as an organization and externally with donors, you’re not alone. We’ve had several clients reach out for our perspective.
Read on for more about the attack, how nonprofits are responding and our advice for what you should be doing now and in the future.
What nonprofits need to know
On July 16, hundreds of nonprofits across the globe received notice of a ransomware attack on Blackbaud that occurred in May 2020.
The attackers gained access to donor data and were able to remove a subset of data from their self-hosted environment. The attack did not include their CRM or eCRM solutions.
Although this stolen data contains no encrypted data, passwords or financial details, it could include personal information, student and donor ID numbers, addresses and contact details, donations, records of an engagement or other activities and professional details.
All of this information is highly valuable in a targeted phishing attack.
Blackbaud released a statement saying they paid an undisclosed amount to the ransomware attackers for a “certificate of destruction.” However, it may be difficult to determine whether copies of this information were made before the original data was destroyed.
How other organizations are responding
As this incident gains global attention, nonprofits are weighing how to respond.
Some organizations have chosen to share the breach with their donors. This has happened in several ways, but the most common has been through a notice on their website, through email or via direct mail.
Others have taken it a step further, making the choice to end their contracts with Blackbaud.
And while these conversations and tough decisions happen internally, nations like the United Kingdom are investigating the delay in notice. Under the General Data Protection Regulation (GDPR), significant data breaches must be reported by companies to authorities within 72 hours of learning of the incident.
Since this took place in May - and organizations weren’t notified until July - Blackbaud’s compliance is being called into question.
What nonprofits should be doing
We frequently discuss the importance of adopting a data-driven future. But to do this effectively, we must all also embrace a data-centric security strategy.
Nonprofits have a duty to act as responsible stewards of their donors’ data. Recent events should serve as a reminder to conduct frequent data governance review policies.
How can you do this?
We suggest you begin to review your internal policies and your web privacy statements to understand your organization’s requirements.
When something like this happens, make sure communication to the members of your organization is clear and consistent.
Then, determine whether your organization will be sending out communication regarding the breach to donors, volunteers and event attendees. Here’s what you should consider as you make this decision:
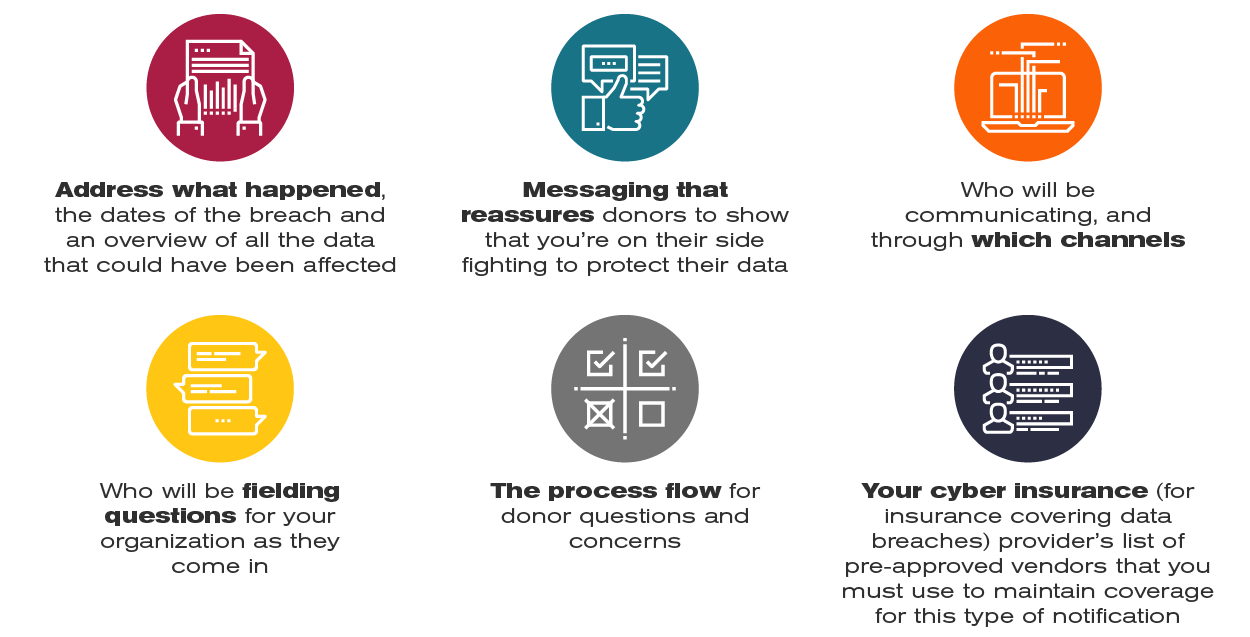
As individual privacy concerns grow and more data privacy regulations appear, it’s important to also assess your third-party vendor and agency compliance policies.
Moving forward, these assessments should be standard practice for your organization. If adopted, they can help ensure you are prepared for any incidents that arise in the future.
Want more info about donor privacy?
Check out these related pieces:





Leave a comment: